Towven.com – The digital landscape is constantly evolving, and with it, the threats posed by cybercriminals.
Traditional security approaches built on centralized firewalls and perimeter defenses are becoming increasingly inadequate in the face of sophisticated attacks.
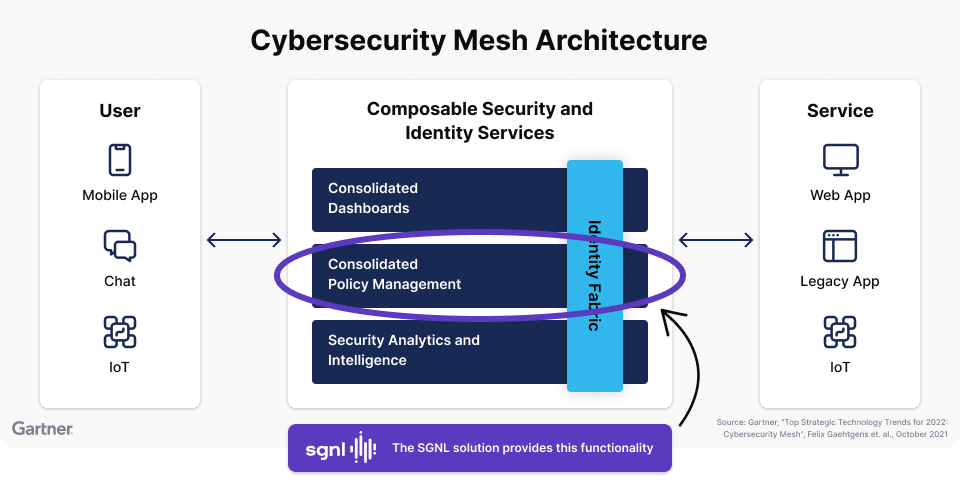
This necessitates a paradigm shift in cybersecurity strategy. Enter the cybersecurity mesh architecture (CSMA).
It emerges as a distributed security model that transcends the limitations of traditional approaches, offering a more flexible and scalable solution for securing an organization’s digital assets regardless of location.
This article delves into the captivating world of cybersecurity mesh architecture, exploring its core principles, the advantages it offers, and its potential to transform the way organizations approach cybersecurity.
Beyond the Firewall: Unveiling the Core Principles of Cybersecurity Mesh Architecture (CSMA)
Cybersecurity mesh architecture (CSMA) departs from the centralized security model. It leverages several key principles to create a more dynamic and adaptable security posture:
-
Distributed Security Fabric: CSMA does not rely on a single point of control. Instead, it distributes security intelligence and enforcement capabilities across the entire network infrastructure. This distributed approach makes it more resilient to attacks, as compromising one node doesn’t cripple the entire security system.
-
Identity-Centric Security: CSMA prioritizes identity as the core security perimeter. This means access control decisions are based on user identity and device trust, regardless of location or network connection.
-
Microsegmentation: CSMA utilizes microsegmentation techniques to divide the network into smaller, more manageable segments. This allows for granular control over access and minimizes the potential damage caused by a security breach.
-
API Integration: CSMA leverages Application Programming Interfaces (APIs) to seamlessly integrate various security tools and services within the mesh architecture. This allows for centralized management and comprehensive security visibility.
-
Automation and Orchestration: CSMA heavily relies on automation and orchestration to streamline security operations. This includes automating tasks like threat detection, incident response, and security policy enforcement.
These core principles of cybersecurity mesh architecture (CSMA) work together to create a more dynamic, adaptable, and scalable security posture, better suited to protect organizations in today’s complex and ever-changing threat landscape.
Beyond the Silo: The Advantages of Cybersecurity Mesh Architecture (CSMA)
Cybersecurity mesh architecture (CSMA) offers several advantages over traditional security approaches:
-
Improved Security Posture: The distributed nature of CSMA makes it more resilient to attacks. Additionally, the focus on identity-centric security and microsegmentation minimizes the impact of breaches.
-
Enhanced Visibility and Control: CSMA provides a centralized view of security posture across the entire network infrastructure. This improved visibility allows for better control over access and enables proactive threat detection.
-
Scalability and Adaptability: CSMA is inherently scalable and can be easily adapted to accommodate new devices, applications, and evolving security needs. This is crucial for organizations with dynamic IT environments.
-
Simplified Security Management: CSMA leverages automation and orchestration to streamline security operations. This reduces manual workload and allows security teams to focus on strategic initiatives.
-
Integration with Existing Security Tools: CSMA is designed to integrate seamlessly with existing security tools and services. This allows organizations to leverage their existing investments while building a more robust security posture.
-
Reduced Complexity: CSMA simplifies security management by eliminating the need for complex configuration and management of centralized firewalls. This can be particularly beneficial for organizations with limited security resources.
These advantages make cybersecurity mesh architecture (CSMA) an attractive solution for organizations of all sizes seeking to improve their security posture and adapt to the ever-evolving threat landscape.
Beyond the Hype: Challenges and Considerations for Cybersecurity Mesh Architecture (CSMA)
While cybersecurity mesh architecture (CSMA) offers significant advantages, there are some challenges and considerations to address for successful implementation:
-
Complexity of Implementation: Transitioning from a centralized security model to a CSMA can be complex. Careful planning, integration with existing security tools, and skilled personnel are crucial for successful implementation.
-
Skills Gap: Effectively utilizing a CSMA may require security teams to develop new skills in areas like automation, orchestration, and API integration.
-
Cost Considerations: While CSMA can streamline security operations in the long run, the initial investment in new technologies and personnel training can be significant.
-
Vendor Lock-In: Organizations need to carefully evaluate CSMA solutions to avoid vendor lock-in and ensure compatibility with existing security tools.